Printers that have a direct network connection often include a built-in web server that lets you manage the printer from any browser on the network. The following figure shows the home page for an HP LaserJet 400 M401dne printer. This web interface lets you view status information about the printer and check the printer’s configuration. A network of experienced technologists focused on MVP product development, strategic business development & sales hunting, specifically for mobile and cloud- based disruptive technologies.
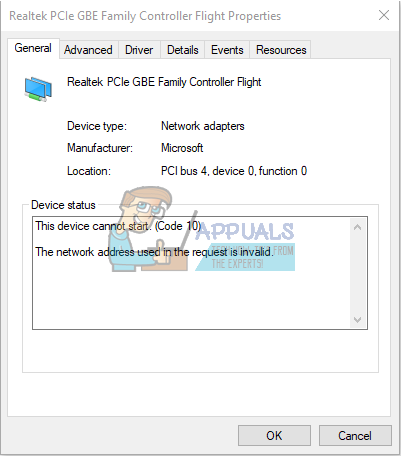
Microsoft has quietly added a built-in network packet sniffer to the Windows 10 October 2018 Update, and it has gone unnoticed since its release.
A packet sniffer, or network sniffer, is a program that monitors the network activity flowing over a computer down to an individual packet level.
This can be used by network administrators to diagnose networking issues, see what types of programs are being used on a network, or even listen in on network conversations sent via clear text.
While Linux users always had the tcpdump tool to perform network sniffing, Windows users have had to install third-party programs such as the Microsoft Network Monitor and Wireshark.
This all changed when Microsoft released the October 2018 Update as now Windows 10 comes with a new 'Packet Monitor' program called pktmon.exe.
Built-in packet sniffer comes to Windows 10
With the release of the Windows 10 October 2018 Update, Microsoft quietly added a new network diagnostic and packet monitoring program called C:Windowssystem32pktmon.exe.
This program has a description of 'Monitor internal packet propagation and packet drop reports', which indicates it is designed for diagnosing network problems.
Similar to the Windows 'netsh trace' command, it can be used to perform full packet inspection of data being sent over the computer.
This program has no mention on Microsoft's site that we could find, and we had to learn how to use it by playing with the program.
Thankfully it includes a fairly extensive help system that can be used by typing 'pktmon [command] help'.
For example, pktmon filter help, will give you the help screen for the filter command.
To learn how to use Pktmon, I strongly suggest you read through the help documentation and play around with the program. We have also provided an example in the next section to help you get started.
Using Pktmon to monitor network traffic
Unfortunately, diving into the full feature set of Pktmon is outside of the scope of this article, but we wanted to show you a basic example of how you can use the tool.
Open Interface Network & Wireless Cards Drivers
For our example, we will use Pktmon to monitor FTP traffic from the computer it is run on.
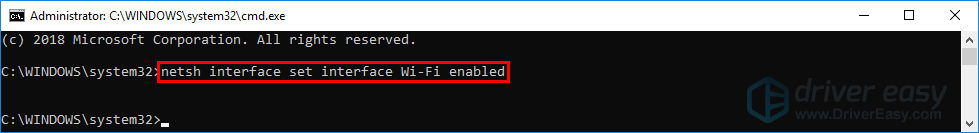
To do this, we first need to launch a Windows 10 elevated command prompt as Pktmon requires administrator privileges.
We then need to create two packet filters that tell Pktmon what traffic to monitor, which in our example will be the traffic on TCP ports 20 and 21.
These filters can be created by using the pktmon filter add -p [port] command for each port we want to monitor.
You can then use the pktmon filter list command to see the packet filters we just created.
To start monitoring for packets communicating with TCP ports 20 and 21, we need to use the pktmon start --etw command.
Once executed, pktmon will log all packets on ALL network interfaces on the device to a file called PktMon.etl and only record the first 128 bytes of a packet.
To make it log the entire packet and only from a specific ethernet device, you can use the -p 0 (capture entire packet) and -c 13 (capture only from the adapter with ID 13) arguments.
To determine what ID your adapters are, you can run the command pktmon comp list command
When we combine all the arguments, we get a final command of:
Pktmon will now quietly run while capturing all packets that match our inputted filters.
To stop capturing packets, enter the pktmon stop command, and a log file called PktMon.etl will have been created in the same folder that contains the raw captured data.
This data in this file is not directly usable, so you need to convert it to a human-readable text format with the following command:
Even converted into text, it is not going to give you the full packets, but only a summary of the network traffic as shown below.
To benefit from the captured data, I suggest you download and install the Microsoft Network Monitor and use it to view the ETL file.
Using Network Monitor, you can see the full packet that was sent, including any clear-text information.
For example, below you can see a packet containing the clear-text password we entered when logging into this FTP test site.
When done using the Pktmon program, you can remove all created filters using the command:
Real-time monitoring and pcapng support coming soon
With the upcoming release of the Windows 10 May 2020 Update (Windows 10 2004), Microsoft has updated the Pktmon tool to allow you to display monitored packets in real-time and to convert ETL files to the PCAPNG format.
In the version of Pktmon coming in the next feature update, you can enable real-time monitoring using the -l real-time argument.
This will cause the captured packets to be displayed directly to the screen while also saving it to the ETL file.
Microsoft is also adding the ability to convert ETL files to the PCAPNG format so that they can be used in programs like Wireshark.
Once the file has been converted into the PCAPNG format, they can be opened into Wireshark so you can view the network communication better.
Once again, these features are not available in Windows 10 1903/1909, and will be coming to Windows 10 2004 when it's released at the end of the month.
Update 5/16/20: Added other new features coming with Windows 10 2004
Related Articles:
COVID-19 Dataset
Update: Data for January 2021 is out now!
While we are sad to be tracking much fewer aircraft these days, we have created a much requested research dataset for all flights that we have tracked since 2019. You can find more information here and the dataset here.
Relatedly, you can check out the Bank of England using OpenSky data to nowcast economic indicators in the COVID-19 crisis.
Extended: Win Prizes in the Aircraft Localization Competition
The Aircraft Localization Competition is back!
Update: Round 2 is extended! Compete on real-world OpenSky data and show your localization skills until January 31, 2021!
We have teamed up with the AICrowd data science platform to bring aircraft localization research to the next level. You can take part and win a trip to our next OpenSky Symposium among other significant prizes! Check out all information at AI Crowd: Aircraft Localization Competition and bring your submissions to advance air traffic localization.
The 8th OpenSky Symposium: November 12/13
Open Interface Network & Wireless Cards Drivers
We are very proud of our community's awe-inspiring contributions at the 8th OpenSky Symposium! You can (re-)watch the videos on our Youtube channel and now read the proceedings!
OpenSky and ATCO2 Project
We are excited to and proud to be part of a project called “AuTomatic COllection and processing of voice data from Air-Traffic Communications” (ATCO2), a project funded by European Commission under Horizon2020 framework.
ATCO2 project aims at developing automatic ATC voice data transcription system. The outcome of the project can potentially be used to make aviation safer and more efficient in so many ways. June fabrics driver.
The good news is that you, too, can participate in the project! We are looking for people to annotate and check the quality of automatically transcribed voice data.
If interested, contact us be sending e-mail to This email address is being protected from spambots. You need JavaScript enabled to view it. for further details. More info can be found from our forum and project website www.atco2.org
Join the OpenSky Network Team!
Long story short – there is so much going on around OpenSky Network, that we are in desperate need of highly motivated Software Engineers.
There are paid full-time posts available, ideally to be in Zurich, Switzerland or Tallinn, Estonia (with remote locations also possible.)
More info about the role in our forum or This email address is being protected from spambots. You need JavaScript enabled to view it.
About the OpenSky Network
The OpenSky Network is a non-profit community-based receiver network which has been continuously collecting air traffic surveillance data since 2013. Unlike other networks, OpenSky keeps the complete unfiltered raw data and makes it accessible to academic and institutional researchers. With over 20 trillion ADS-B, Mode S, TCAS and FLARM messages collected from more than 3000 sensors around the world, the OpenSky Network exhibits the largest air traffic surveillance dataset of its kind. The mission of our non-profit association is to support open global air traffic research by universities and other not-for-profit institutions.
Aircraft Database
Find and track aircraft with our comprehensive database. You can also add and update information!
Unfiltered live API
Our live API comes with Java and Python bindings, but it can be used with any language that supports JSON-based REST APIs.
OpenSky Explorer
Browse through historical air traffic with our OpenSky Explorer.
Air Traffic Statistics
See up-to-date statistics on air traffic and our network on our Network Facts page.
